Time Needed To Crack Aes Encryption

What is Data Encryption Standard (DES)? The Data Encryption Standard (DES) is an outdated symmetric- key method of data encryption. DES works by using the same key to encrypt and decrypt a message, so both the sender and the receiver must know and use the same private key. Once the go- to, symmetric- key algorithm for the encryption of electronic data, DES has been superseded by the more secure Advanced Encryption Standard (AES) algorithm. By submitting your personal information, you agree that Tech.
Learn about asymmetric encryption, symmetric encryption, key strength, public-key encryption, pre-shared key encryption, and how it all fits together.
Encryption Algorithms - asymmetric encryption algorithms, symmetric encryption algorithms, types of encryption algorithms, strong encryption algorithms, DES. Data Encryption Standard (DES) was a widely-used method of data encryption using a private (secret) key that was judged so difficult to break by the U.S.
Target and its partners may contact you regarding relevant content, products and special offers. You also agree that your personal information may be transferred and processed in the United States, and that you have read and agree to the Terms of Use and the Privacy Policy. Originally designed by researchers at IBM in the early 1. DES was adopted by the U. S. It was the first encryption algorithm approved by the U. S. This ensured that DES was quickly adopted by industries such as financial services, where the need for strong encryption is high. The simplicity of DES also saw it used in a wide variety of embedded systems, smart cards, SIM cards and network devices requiring encryption like modems, set- top boxes and routers.
DES key length and brute- force attacks. The Data Encryption Standard is a block cipher, meaning a cryptographic key and algorithm are applied to a block of data simultaneously rather than one bit at a time. To encrypt a plaintext message, DES groups it into 6. Each block is enciphered using the secret key into a 6. The process involves 1. Decryption is simply the inverse of encryption, following the same steps but reversing the order in which the keys are applied.
For any cipher, the most basic method of attack is brute force, which involves trying each key until you find the right one. The length of the key determines the number of possible keys - - and hence the feasibility - - of this type of attack. DES uses a 6. 4- bit key, but eight of those bits are used for parity checks, effectively limiting the key to 5. Hence, it would take a maximum of 2^5. Even though few messages encrypted using DES encryption are likely to be subjected to this kind of code- breaking effort, many security experts felt the 5. DES was adopted as a standard. Even so, DES remained a trusted and widely used encryption algorithm through the mid- 1.
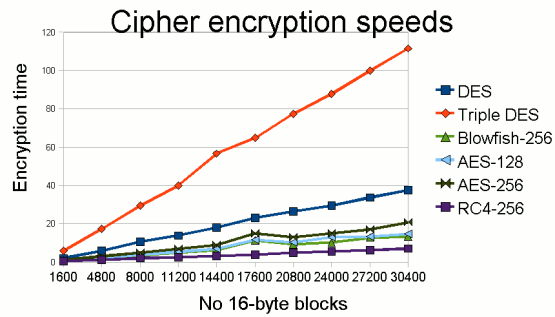
However, in 1. 99. Electronic Frontier Foundation (EFF) decrypted a DES- encoded message in 5. By harnessing the power of thousands of networked computers, the following year EFF cut the decryption time to 2. Apart from providing backwards compatibility in some instances, reliance today upon DES for data confidentiality is a serious security design error in any computer system and should be avoided. There are much more secure algorithms available, such as AES. Much like a cheap suitcase lock, DES will keep the contents safe from honest people, but it won't stop a determined thief. Successors to DESEncryption strength is directly tied to key size, and 5.
So in 1. 99. 7, the National Institute of Standards and Technology (NIST) announced an initiative to choose a successor to DES; in 2. Advanced Encryption Standard as a replacement. The Data Encryption Standard (FIPS 4. May 2. 00. 5, though Triple DES (3. DES) is approved through 2.
DES performs three iterations of the DES algorithm; if keying option number one is chosen, a different key is used each time to increase the key length to 1. However, due to the likelihood of a meet- in- the- middle attack, the effective security it provides is only 1. DES encryption is obviously slower than plain DES. Legacy of DESDespite having reached the end of its useful life, the arrival of the Data Encryption Standard served to promote the study of cryptography and the development of new encryption algorithms. Until DES, cryptography was a dark art confined to the realms of military and government intelligence organizations.
The open nature of DES meant academics, mathematicians and anyone interested in security could study how the algorithm worked and try to crack it. As with any popular and challenging puzzle, a craze - - or in this case, a whole industry - - was born.
Advanced Encryption Standard Algorithm Validation List. The page provides technical information about implementations that have been validated as conforming to the. Advanced Encryption Standard (AES) Algorithm, as specified in Federal Information Processing. Standard Publication 1. Advanced Encryption Standard.
The list below describes implementations which have been validated as correctly implementing the AES algorithm, using the tests found in. The Advanced Encryption Standard Algorithm Validation Suite (AESAVS). This testing is performed by NVLAP. Cryptographic And Security Testing (CST) Laboratories. The implementations below consist of software, firmware, hardware, and any combination thereof.
The National Institute of Standards. Technology (NIST) has made every attempt to provide complete and accurate information about the implementations described. This list is ordered in reverse numerical order, by validation number.
Thus, the more recent validations are located closer to. The column after the Validation Date column contains information indicating what modes and. Three categories of PT and AAD lengths are tested if supported. Plaintext length = 0; AAD length = 0. Plaintext length = 0; AAD length multiple of 1. Online Tv V1 23 2011 Full Size. Plaintext length = 0; AAD length not multiple of 1.
Plaintext length multiple of 1. AAD length = 0. 5. Plaintext length multiple of 1. AAD length multiple of 1. Plaintext length multiple of 1. AD length not multiple of 1. Plaintext length not multiple of 1.
AAD length = 0. 8. Plaintext length not multiple of 1. AAD length multiple of 1. Plaintext length not multiple of 1. AAD length not multiple of 1. If an IV is generated internally, the laboratory must affirm that the IV is.
NIST SP8. 00- 3. 8D, Section 8. Section 8. 2. 2. Values were tested in combination with AAD lengths)AAD Lengths tested Values tested (See explanation above.
Values were tested in combination with PT lengths)GMACSupported/Not Supported(For XPN, only 9. Bit. IV applies)9.
Bit. IVSupported/Not Supported. IV Generated. Internally (using Section 8. Section 8. 2. 2)/Externally. IV Lengths Tested. Values tested XPNSupported/Not Supported. Salt Generated (only if XPN Supported)Internal/External. For the CMAC authentication mode of operation, this information consists of the key sizes (1.
KS 1. 28,1. 92,2. The product implements the algorithms that provide the non- linear substitution tables, and also supports to update the secret keys dynamically to protect the secret keys under the white- box attacks environment. Data Len Range. (Payload Length Range. Nonce Length(s). (Tag Length(s). With best in class networking and security in a single platform, these best suited for enterprise data centers, campuses, and regional headquarters. With best in class networking and security in a single platform, SRX1.
Lakeview Canyon Road, Suite 1. Westlake Village.
USA- Boris Maliatski. TEL: 9. 49- 8. 61- 3. OTU4 AES- 2. 56 GCM CTRPart # M1xx. S/M2xx. S. AES. Data Len Range.
Payload Length Range. Nonce Length(s). (Tag Length(s). GCM(KS: AES. Data Len Range. Payload Length Range. Nonce Length(s). (Tag Length(s).
CMAC (Generation/Verification. KS: 1. 28; Block Size(s). KS: 1. 92; Block Size(s).
KS: 2. 56; Block Size(s). GCM(KS: AES. Data Len Range. Payload Length Range. Nonce Length(s). (Tag Length(s). CMAC (Generation/Verification. KS: 1. 28; Block Size(s).
KS: 1. 92; Block Size(s). KS: 2. 56; Block Size(s). GCM(KS: AES. It provides cryptographic functions. Davie Street. Raleigh. USA- Jaroslav Reznik.
Open. SSL (no AVX2/AVX, x. Data Len Range. (Payload Length Range.
Nonce Length(s). (Tag Length(s). CMAC (Generation/Verification. KS: 1. 28; Block Size(s). KS: 1. 92; Block Size(s). KS: 2. 56; Block Size(s). GCM(KS: AES. Davie Street. Raleigh. 2. 76. 01.
USA- Jaroslav Reznik. Open. SSL (no AVX2/AVX, x. Data Len Range. (Payload Length Range. Nonce Length(s). (Tag Length(s).
CMAC (Generation/Verification. KS: 1. 28; Block Size(s).
KS: 1. 92; Block Size(s). KS: 2. 56; Block Size(s). GCM(KS: AES. Davie Street. Raleigh. 2. 76. 01. USA- Jaroslav Reznik.
Open. SSL (no AVX2/AVX/AESNI, x. Data Len Range. (Payload Length Range. Nonce Length(s). (Tag Length(s). CMAC (Generation/Verification. KS: 1. 28; Block Size(s). KS: 1. 92; Block Size(s). KS: 2. 56; Block Size(s).
GCM(KS: AES. Davie Street. Raleigh. 2. 76. 01. USA- Jaroslav Reznik. Open. SSL (no AVX2/AVX/AESNI, x. Data Len Range. (Payload Length Range.
Nonce Length(s). (Tag Length(s). CMAC (Generation/Verification. KS: 1. 28; Block Size(s). KS: 1. 92; Block Size(s). KS: 2. 56; Block Size(s). GCM(KS: AES. Davie Street.
Raleigh. 2. 76. 01. USA- Jaroslav Reznik.
Open. SSL (no AVX2/AVX/AESNI/SSSE3, x. Data Len Range. (Payload Length Range.
Nonce Length(s). (Tag Length(s). CMAC (Generation/Verification. KS: 1. 28; Block Size(s).
KS: 1. 92; Block Size(s). KS: 2. 56; Block Size(s). GCM(KS: AES. Davie Street. Raleigh. 2. 76. 01.
USA- Jaroslav Reznik. Open. SSL (no AVX2/AVX/AESNI/SSSE3, x. Data Len Range. (Payload Length Range. Nonce Length(s). (Tag Length(s). CMAC (Generation/Verification. KS: 1. 28; Block Size(s). KS: 1. 92; Block Size(s).
KS: 2. 56; Block Size(s). GCM(KS: AES. 2. 1 in encrypt/decrypt configuration (GCM6- 1. QFE+GCM- 1. 28. QBE)Version 2. Firmware). Aldec Riviera- PRO 2.
GCM(KS: AES. See the description at http: //www. XTS4- 1. 28. FE+XTS4- 1.
BED)Version 2. 1 (Firmware). Aldec Riviera- PRO 2. KS: XTS. 2. 1 in encrypt configuration (XTS4- 1. FE+XTS4- 1. 28. BEE)Version 2. Firmware). Aldec Riviera- PRO 2. KS: XTS. Data Len Range.
Payload Length Range. Nonce Length(s). (Tag Length(s). CMAC (Generation/Verification. KS: 1. 28; Block Size(s). KS: 1. 92; Block Size(s).
KS: 2. 56; Block Size(s). GCM(KS: AES. It can be dynamically linked into applications for the use of general- purpose FIPS 1. Ltd. 7. F., No. 5. Lane 3. 21. Yangguang St., Neihu Dist. Taipei. 1. 14. 91. Taiwan (R. O. C.)- Joe Wang.
TEL: +8. 86- 2- 2. FAX: +8. 86- 2- 2. Kent Horng. TEL: +8.
FAX: +8. 86- 2- 2. TAISYS JUISE- S2. Part # ST3. 3G1. M2. The module is implemented upon Sun Java Card . The device supports three modalities: web- based two- factor authentication, two- factor authentication for protected file decryption and two- factor authentication for digital signature generation. It features the same code base, resiliency, media transcoding, and security technology found in Sonus.
It features the same code base, resiliency, media transcoding, and security technology found in Sonus. The module provides cryptographic functionalities in Motorola Solutions ASTRO IP Dispatch Console products. Data Len Range. (Payload Length Range. Nonce Length(s). (Tag Length(s). CMAC (Generation/Verification.
KS: 1. 28; Block Size(s). KS: 1. 92; Block Size(s). KS: 2. 56; Block Size(s). GCM(KS: AES. Data Len Range. Payload Length Range. Nonce Length(s). (Tag Length(s).
KS: 1. 92; Block Size(s). KS: 2. 56; Block Size(s). GCM(KS: AES. Data Len Range.
Payload Length Range. Nonce Length(s). (Tag Length(s). CMAC (Generation/Verification. KS: 1. 28; Block Size(s). KS: 1. 92; Block Size(s). KS: 2. 56; Block Size(s).
GCM(KS: AES. Data Len Range. Payload Length Range. Nonce Length(s). (Tag Length(s). GCM(KS: AES. Data Len Range. Payload Length Range. Nonce Length(s). (Tag Length(s).
GCM(KS: AES. Davie Street. Raleigh. 2. 76. 01. USA- Jaroslav Reznik. Open. SSL (no AVX2, x. Data Len Range. (Payload Length Range. Nonce Length(s). (Tag Length(s).
CMAC (Generation/Verification. KS: 1. 28; Block Size(s). KS: 1. 92; Block Size(s). KS: 2. 56; Block Size(s). GCM(KS: AES. Davie Street. Raleigh. 2. 76. 01. USA- Jaroslav Reznik.
Open. SSL (no AVX2, x. Data Len Range. (Payload Length Range. Nonce Length(s). (Tag Length(s). CMAC (Generation/Verification. KS: 1. 28; Block Size(s).
KS: 1. 92; Block Size(s). KS: 2. 56; Block Size(s). GCM(KS: AES. Data Len Range. Payload Length Range. Nonce Length(s). (Tag Length(s).